Cyber threats are constantly evolving, and this is due to cybercriminals continuously enhancing their hacking capabilities through new methods and technologies - such as AlienFox.
AlienFox is a modular toolset comprising of various custom tools and open-source utilities, created by multiple authors. Hackers are using AlienFox to collect lists of misconfigured cloud endpoints. When a misconfigured server is identified, the cybercriminal parses exposed environment or configuration files that store sensitive information, such as services enabled and the associated API keys and secrets. If this type of information is compromised, a hacker could potentially gain access to a business’s full network and infrastructure.
The hacking tool allows hackers to target secrets for popular cloud-based email platforms, including 1and1, AWS, Bluemail, Exotel, Google Workspace, Mailgun, Mandrill, Nexmo, Office365, OneSignal, Plivo, Sendgrid, Sendinblue, Sparkpostmail, Tokbox, Twilio, Zimbra, and Zoho. It has been reported that it targets 18 cloud services, including the likes of Wordpress, Laravel, Drupal, Magneto, and Joomla.
As with all new hacking methods and malware, AlienFox is already being widely distributed across the Dark Web, and via other channels. There are also reports that the modular toolkit is already available in multiple versions; the latest version, V4, is reported to feature better code and script organization, allowing hackers to expand the scope and range of businesses to target.
Here’s an example of stolen credentials being shared and circulated:
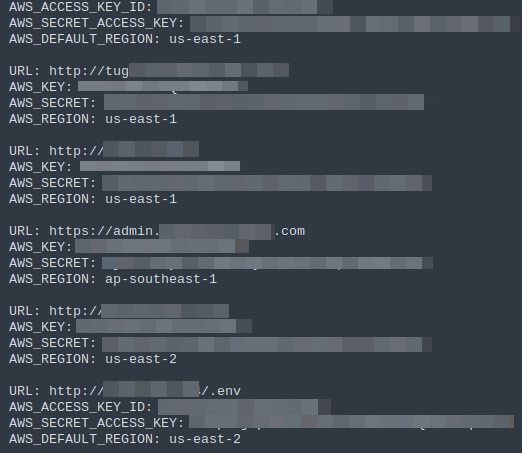
What does this mean for businesses?
Unfortunately, any business, regardless of location, size, or turnover, is a target for cybercriminals. There are always new threats emerging, so the best way to reduce the likelihood of being attacked is by having the correct tools in place to identify and correct any potential holes in your network that hackers can exploit.
Our risk-management solution for businesses, Breach Defence, uses passive scans to check for potential vulnerabilities within your business infrastructure, and ongoing dark web monitoring to alert you if we discover your business or staff credentials being leaked, or discussed within the hacker communities that we monitor.
Along with staff training, phishing simulation, and guides and advice from our support team, our easy-to-use dashboard has been designed to empower businesses to stay on top of the latest cyber threats.
To protect yourself from such attacks, it’s important to have the right measures in place. Here are some additional examples of things to keep in mind:
- Ensure that server configuration is set with proper access controls.
- Ensure file permissions are in place.
- Remove any unnecessary or unused services.
- Use multi-factor authentication on all applications, where possible.
- Be sure to monitor for any unusual or suspicious activity (such as out-of-hours or unknown usernames) to help prevent intrusion.
Protecting yourself from cyberattacks doesn’t have to be complicated. At DynaRisk, we like to keep things simple with our easy-to-use risk management software.
Find out more about how we can help protect your business, by clicking here
