DYNARISK
Breach Defence
All-in-one cyber protection for the 99% of businesses that are SMEs
Increase Engagement
While only a small percentage of policy holders will make a claim, 100% of them can use our solution which deepens engagement and encourages renewals.
MAIN VALUE
DynaRisk empowers small to medium sized businesses to be safer online.
Cyber attacks are constant and are always evolving. 60% of SMEs can go out of business within 6 months of suffering a cyber attack. SMEs need simple yet comprehensive cyber risk management solutions to manage complex cyber risks.
This is why DynaRisk has developed Breach Defence to give SMEs the tools they need to defend against cyber attacks.
Our 4 step approach ensures a business's risks are well mitigated.
Assess
We determine a business's exposure to multiple security issues right away on their first login. We check for vulnerabilities, leaked data records and hacker chatter immediately.
Remediate & Monitor
Users are able to begin mitigating their findings right away, we'll surface any new issues we find and provide detailed guidance for how to address them.
Train & Educate
Employees are both a company's greatest asset and largest exposure to cyber threats. Our platform provides both user education guides and simulated phishing campains to empower staff to improve their cyber safety.
Help & Support
Our multi lingual cyber security experts are always available to help remove a virus, check out a potential phishing email or help a user respond to a ransomware event.
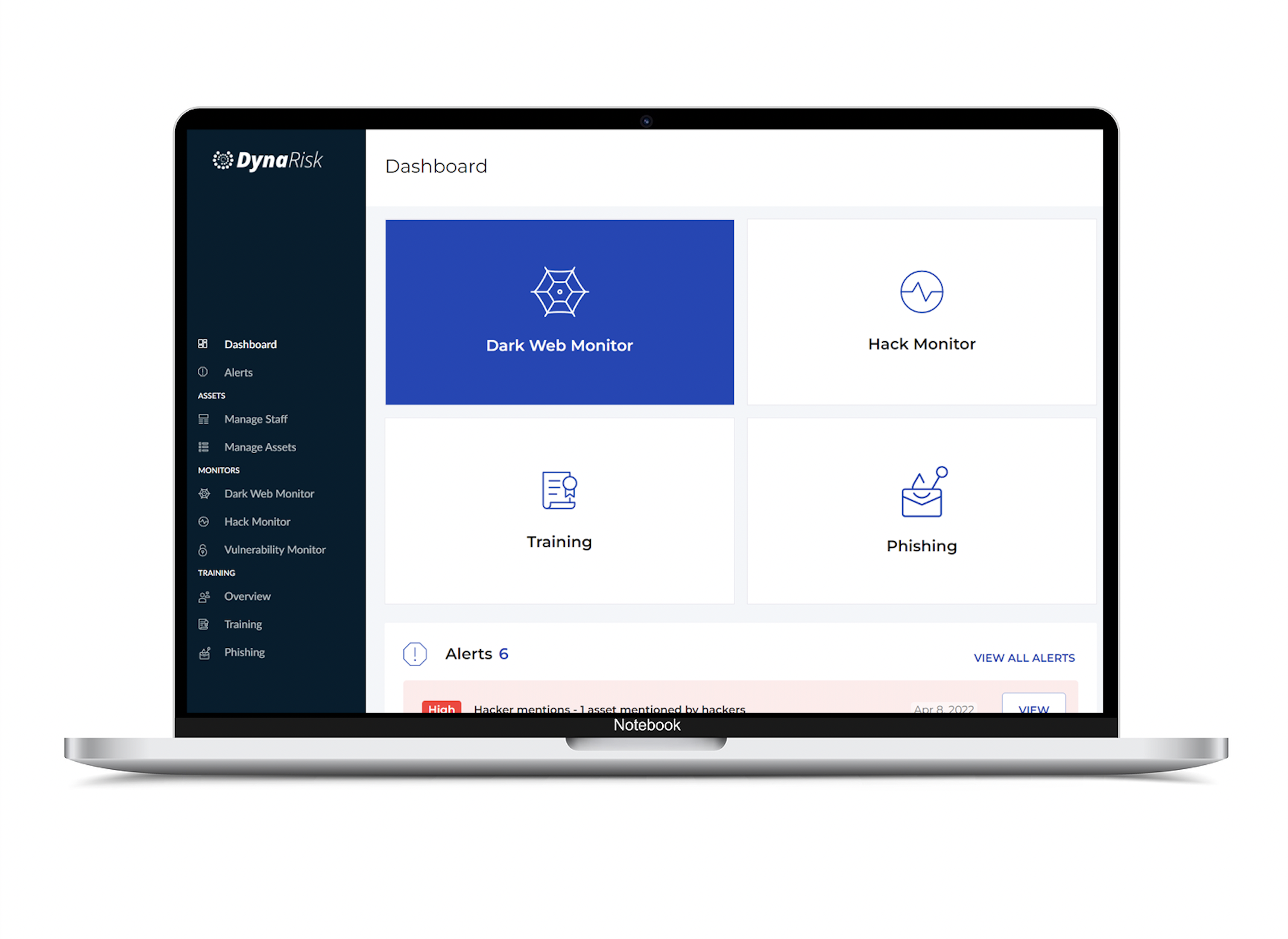
How it works
Our Modules


Exceptional Customer Experience is at our core
We support clients with multi language capability, white labelling and API integrations. Breach Defence is available in 3 languages with more on the way. White label our interface to suit your brand and onboard users seamlessly with our bulk registration and single signon APIs for a smooth customer journey.





